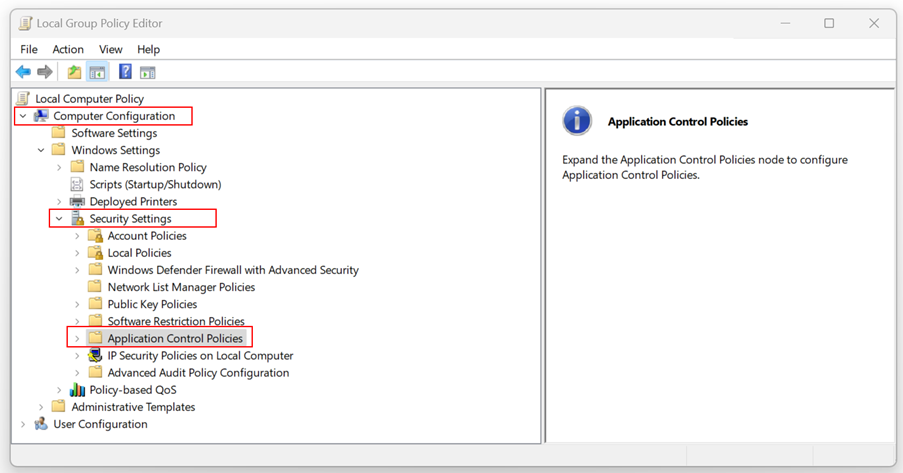
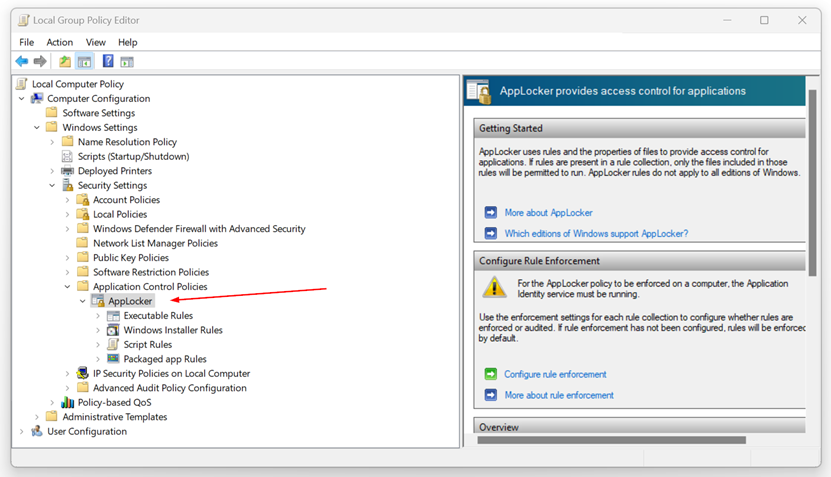
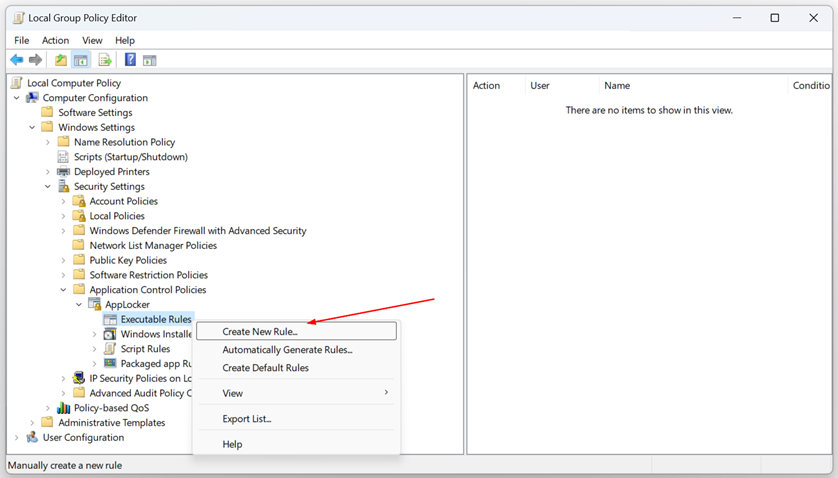
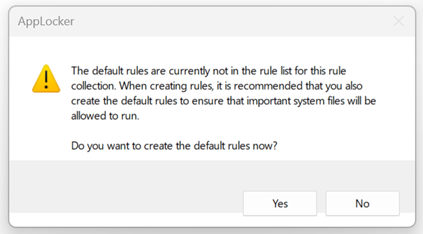
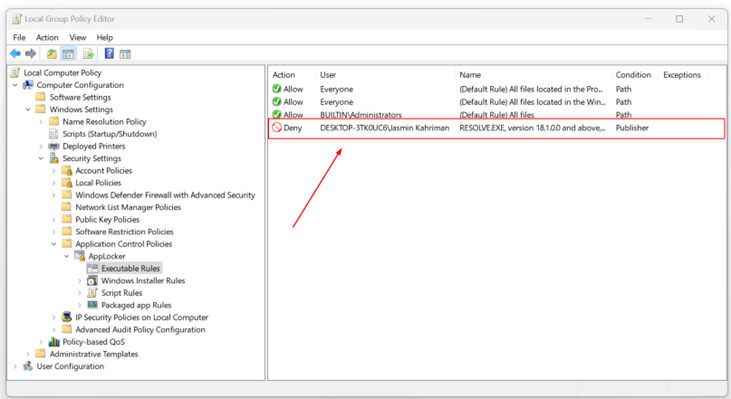
In this article, I will show you how to enable AppLocker and use it in your organization. In order to use AppLocker and create deny rules, we will utilize the Local Group Policy Editor for local computers or the Group Policy Editor for domain-joined machines.
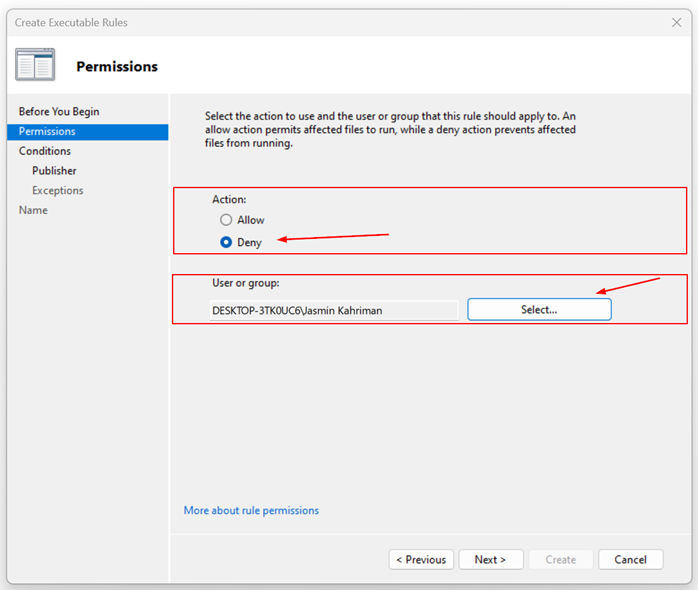
Publisher – related to applications signed by the publisher.Path – related to a file or folder path.File hash – related to applications that are not signed by the publisher.
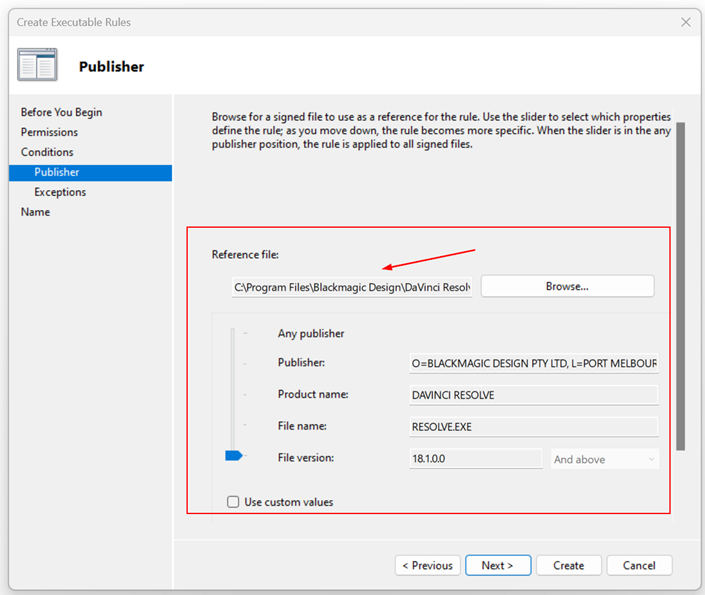
I keep the default settings for the slider. Once done, click Next.
Wrap Up
There are moments when you need to deny certain local or domain users from opening specific applications, files, or folders. By using AppLocker, which is integrated into Windows 11, you can create policies and disable targets by the publisher, path, and file hash. This article covers step-by-step instructions on how to do it.