Unfortunately, cell phones’ vast capabilities also make them an attractive target for cybercriminals seeking personal information. It’s an object that’s hard for them to ignore. Hackers often use cell phones as “entry points” to steal information from institutions like banks. They use the victim’s phone to transmit malicious text messages, making the user responsible for the theft.
How To Remove a Hacker From Your Phone
If your Android or iPhone device has been hacked, you should be prepared to restore it to working order. The article will explain the process.
Step 1: Reset Your Passwords
If you suspect your phone has been hacked, changing your account passwords is the first and most essential step. If you know your personal information was secure, you could rest easily. To do this, you’ll need to identify which of your accounts have been compromised; after that, you can change the passcode to something more secure. If your phone has been hacked, it’s not a good option to keep using the same credentials. If you know which accounts have been compromised, changing their passwords is an effective strategy. Whenever your account is accessed from an unusual place or device, most services will notify you. Act promptly and change your current password. Feel free to alter your current passcode now. You can use the “Forgot your password?” button on the account page to reset your password if someone else has changed it before you. This will initiate an attempt to re-verify your identity (via whatever means are available), with the aim of restoring your account.
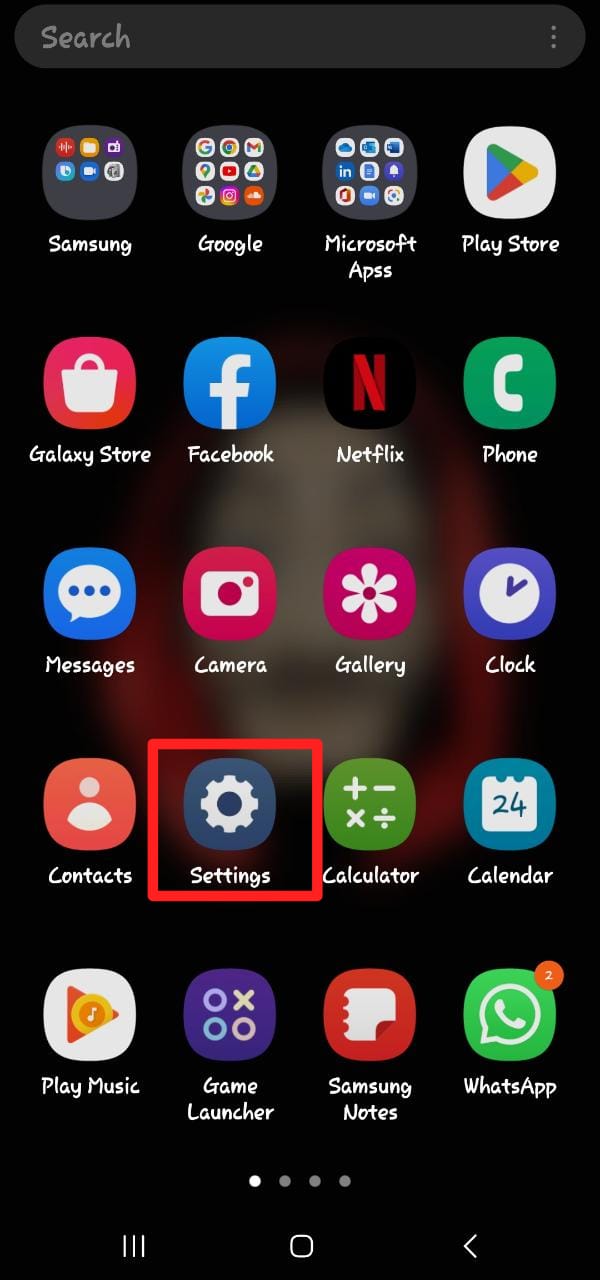
Step 2: Delete Apps
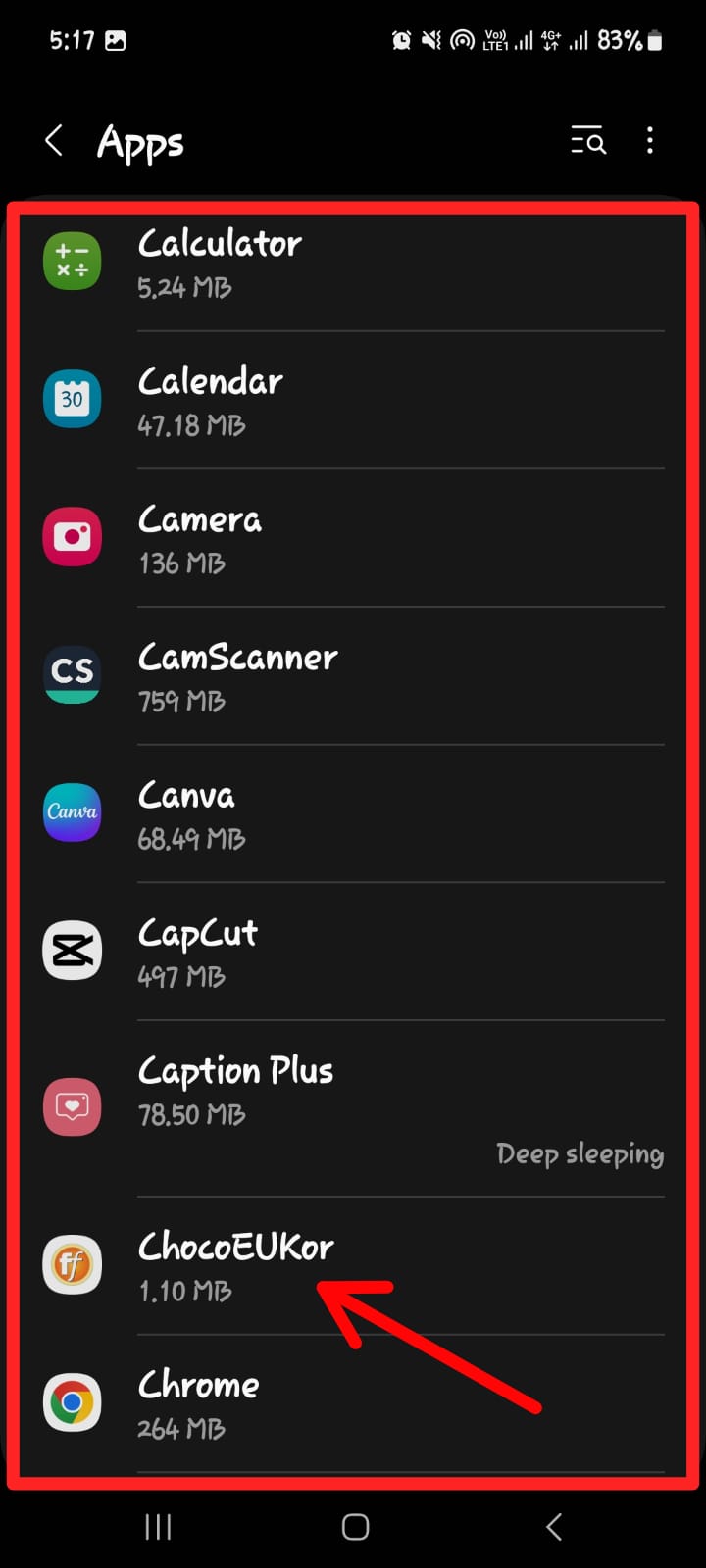
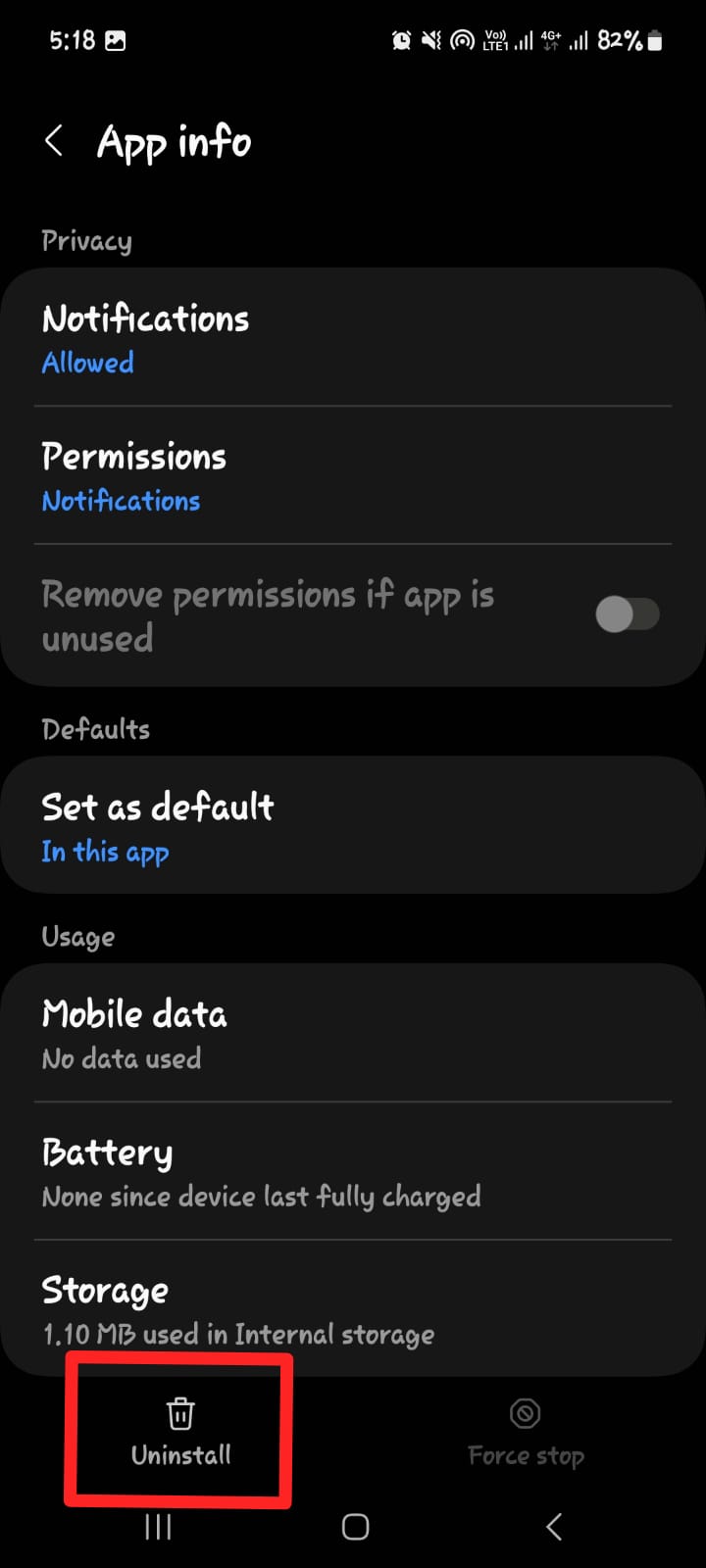
Spy applications are hackers’ most common entry point into a target’s mobile device. A hacker can then repeatedly access your information for as long as required. If your phone has been hacked, you should scan through all of your applications and uninstall any that you don’t remember installing earlier. The same is true if you’re wondering what to do if your iPhone has been compromised.
For Android Users:
If an app refuses to uninstall, disable its administrator privileges by going to Settings > Security > Device Admin apps.
For iPhone Users:
Step 3: Use Antivirus Software
Antivirus software will isolate the malicious app in a sandbox, where it will have no access to the rest of your phone and then erase it automatically. Keep your antivirus program running in the background for continuous protection.
Step 4: Contact Businesses
You should contact any online or conventional businesses with your credit card or banking details. Determine the bank activities you wish to dispute and, if necessary, report them as fraudulent.
Step 5: Manage Wi-Fi
It’s a good idea to turn off Wi-Fi when it’s not in use or when you’re unsure about the security of a Wi-Fi connection, as hackers can access phones through public networks. Many devices have a convenient drop-down menu for this purpose.
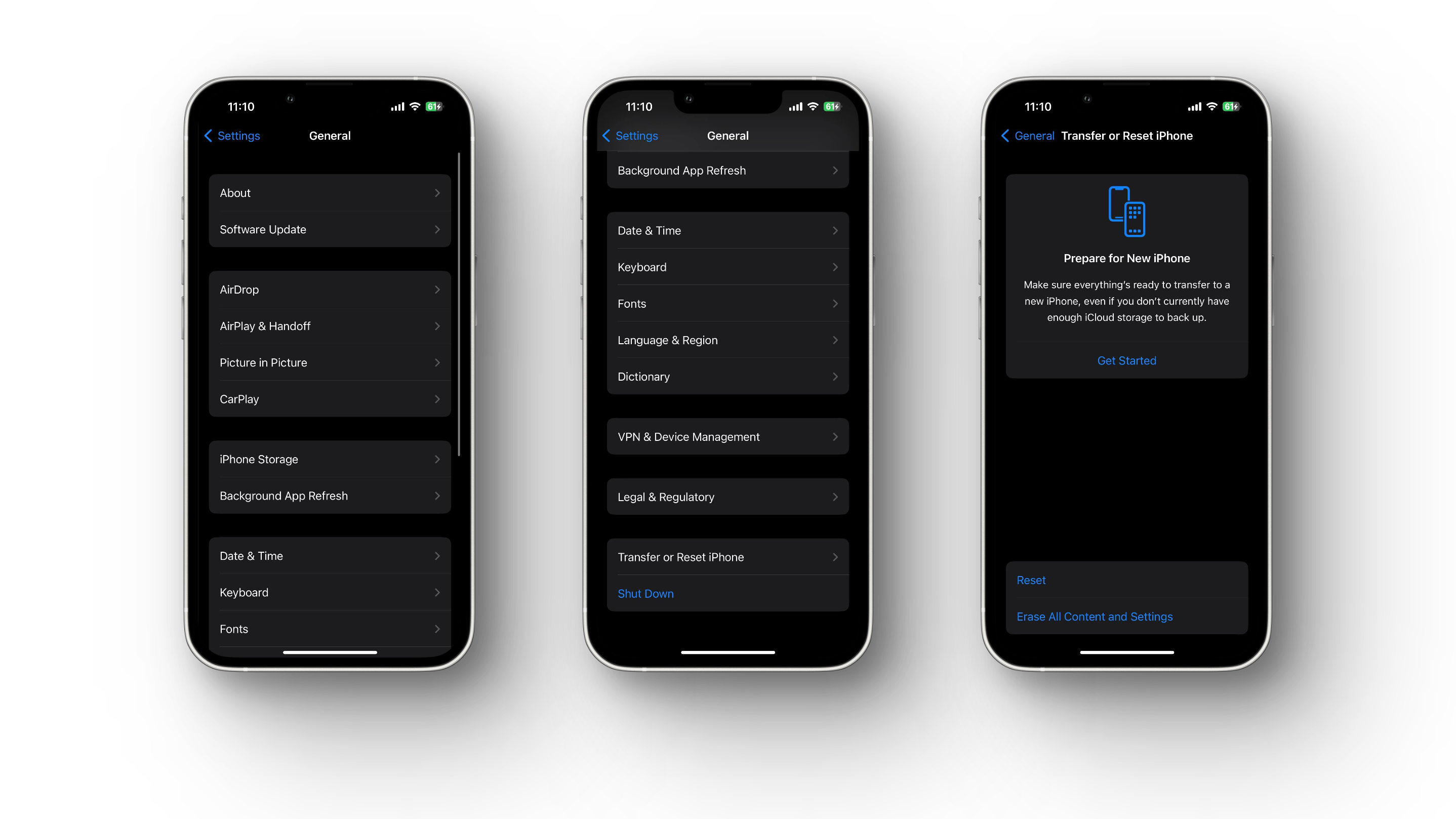
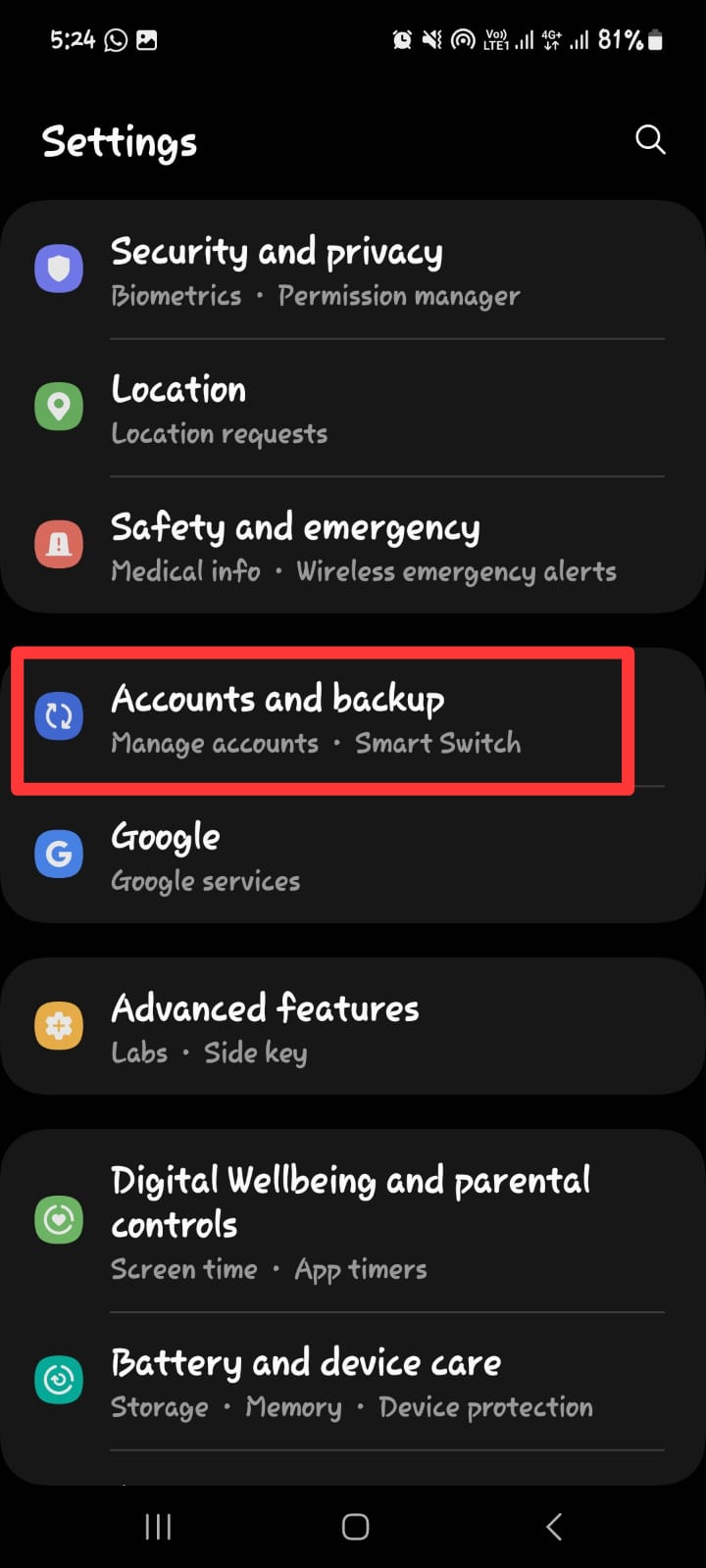
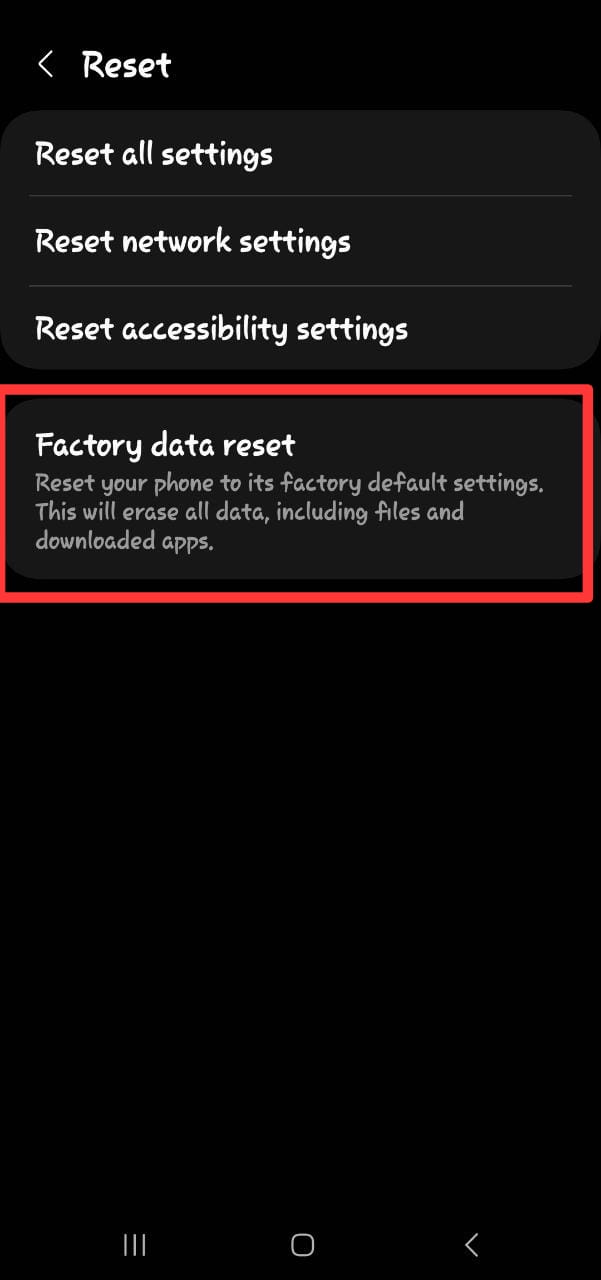
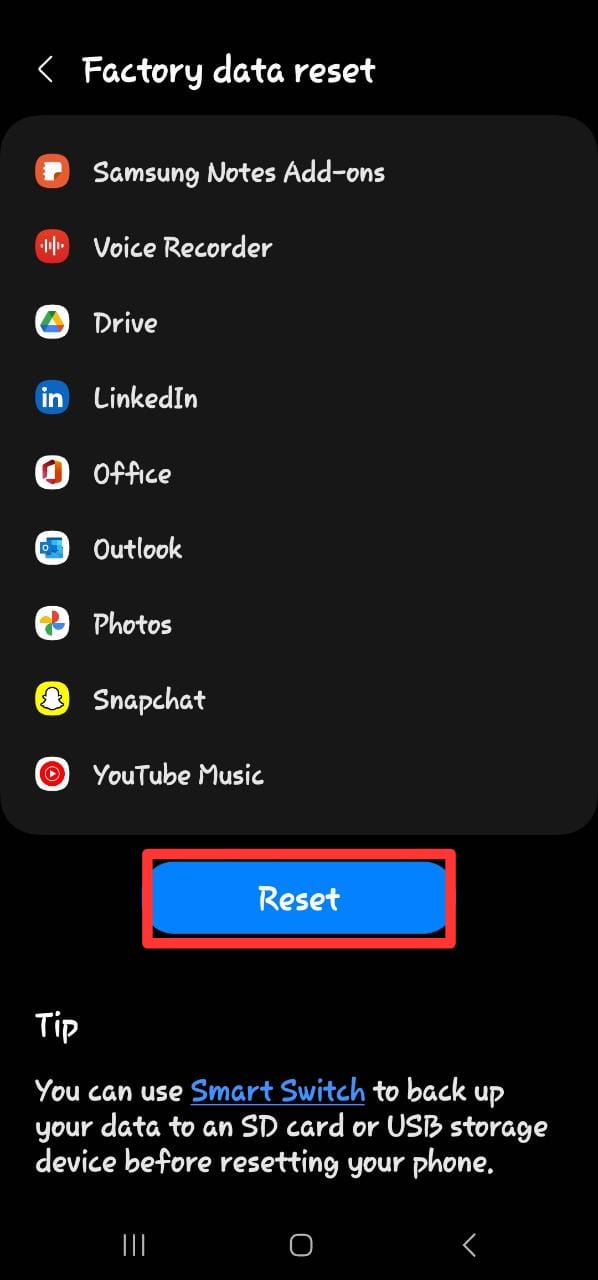
Step 6: Factory-reset your Phone
In addition to the measures above, you can do a full factory reset to return your phone to how it was when you first received it. After a successful backup, proceed as follows:
For iPhone:
For Android:
Step 7: Inform your Contacts
If your phone has been hacked, it’s essential to inform your contacts so they can take steps to protect themselves from phishing emails. or other scams or spam messages. Warn them about the risk of becoming the next victim if they follow any instructions in suspicious messages.
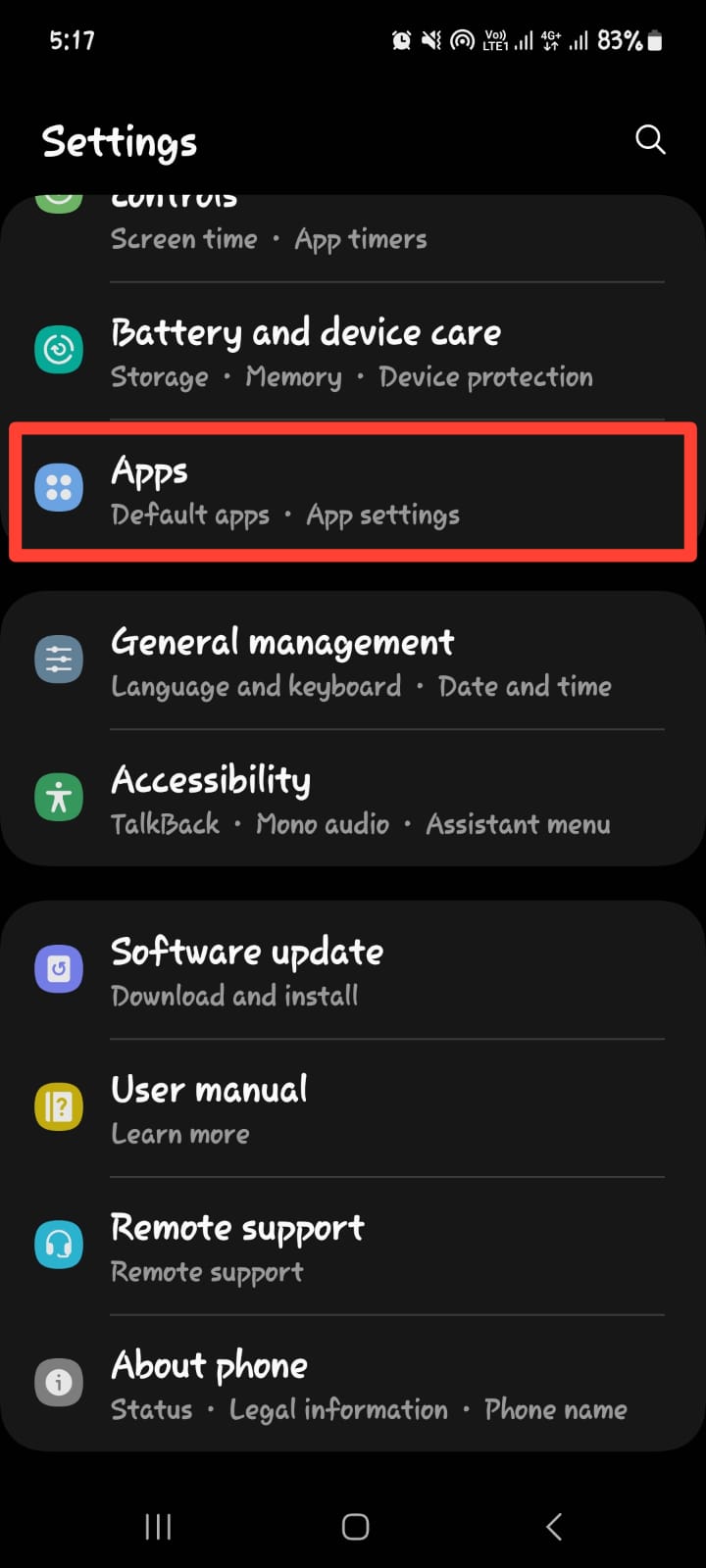
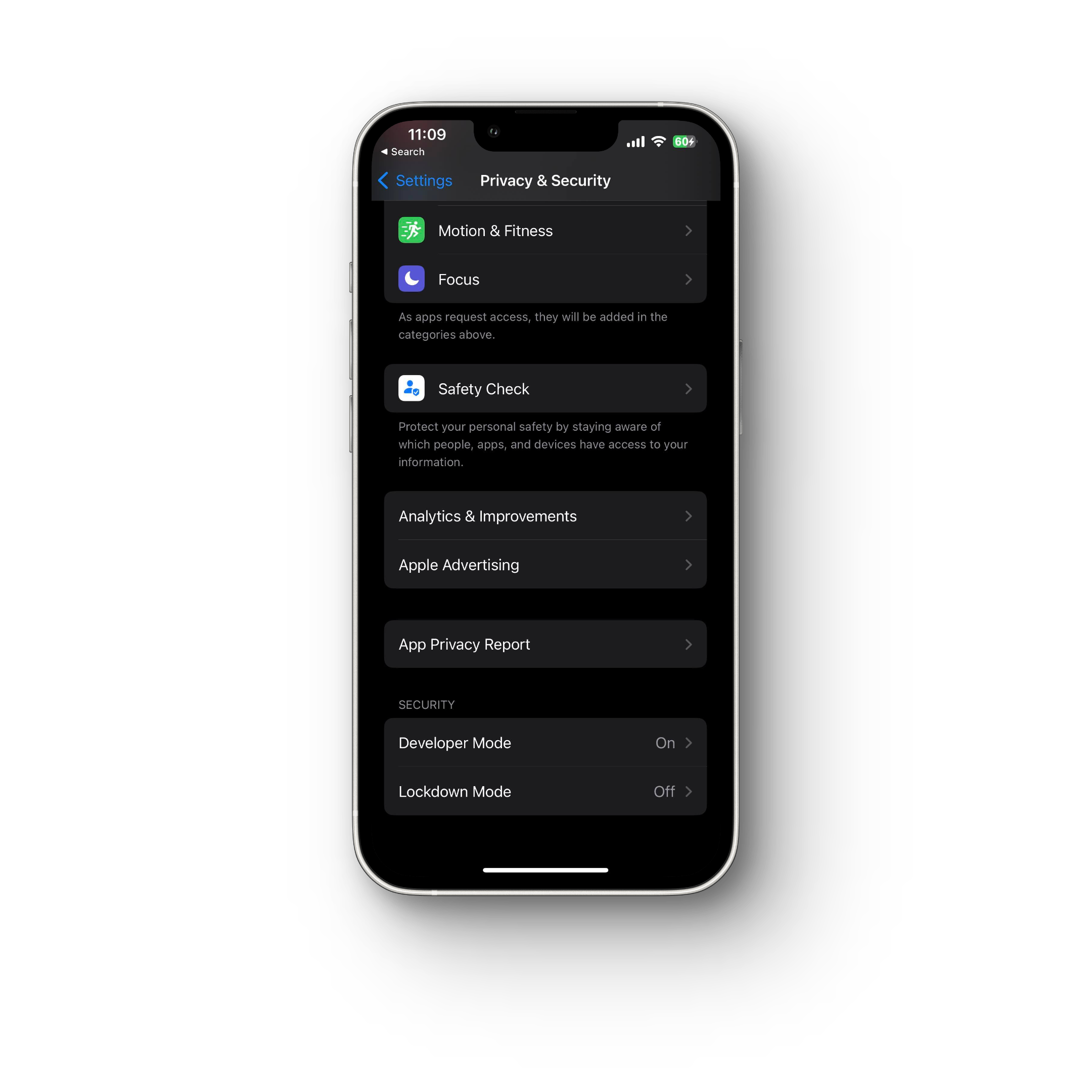
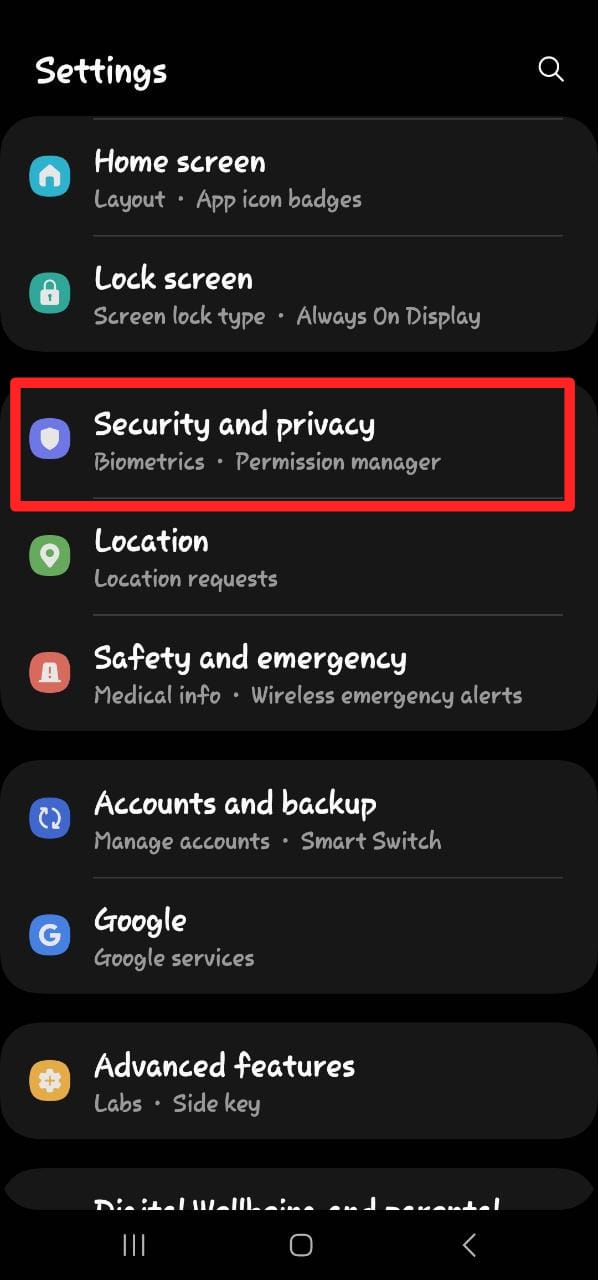
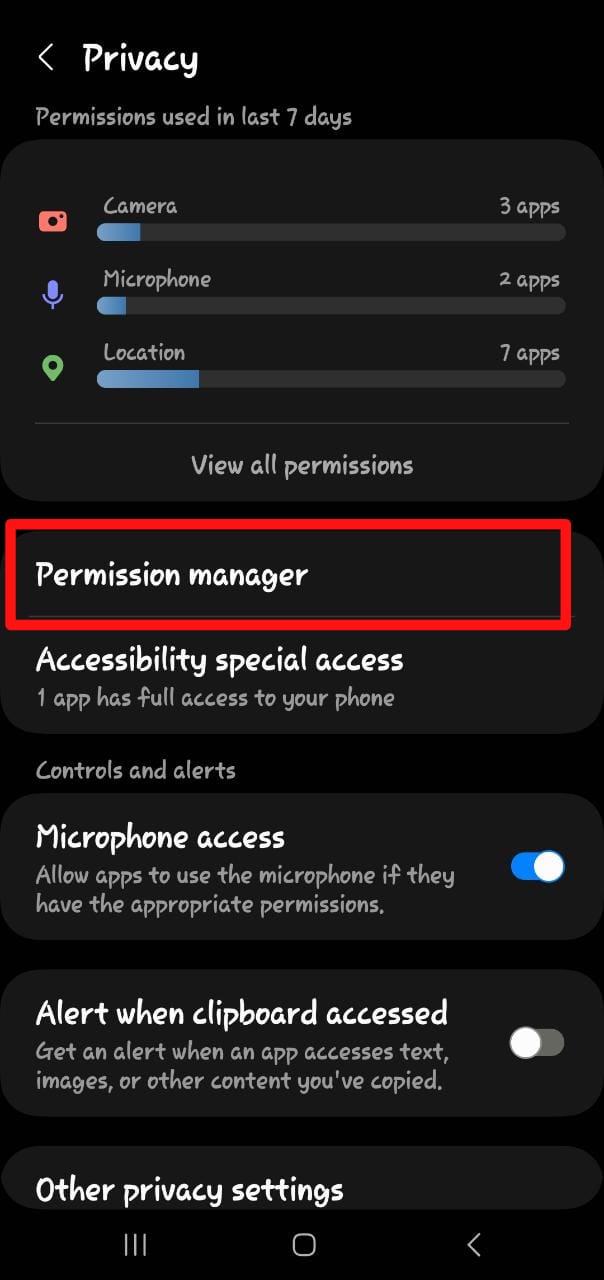
Step 8: Check App Permissions on your Phone
This will enable you to identify any applications on your device with access to private data, such as your current position based on your GPS locations.
For iPhone:
Navigate to Settings > Privacy & Security for different permission levels. Here you can view which apps have access to which features, and you can also restrict access to applications as needed.
For Android:
How to Stop Someone from Hacking Your Phone Again
As more private information moves into digital form and is accessible via mobile devices, safeguarding against phone hacking becomes increasingly essential. Because methods are always changing, you must be careful about security. The best way to safeguard yourself is to be cautious when using digital services, and luckily, many established protocols have been shown to reduce vulnerability to hacking.
Avoid downloading sketchy or disreputable apps
Malware is frequently masked as genuine software and distributed via third-party apps downloaded from unofficial websites rather than the official app stores. It’s best to avoid downloading apps from ads or questionable websites.
Don’t Jailbreak your phone
Jailbreaking increases your vulnerability to hacking because you can now access unofficial app stores. This means you won’t get the newest iOS updates, which can prevent threats like malware and spyware. To keep the jailbreak functional, jailbreakers avoid updating their devices. Because of this, you are even more likely to become a victim of hacking.
Use a VPN to stay safer on the go
Public Wi-Fi networks in airports, hotels, and even libraries can leave your phone vulnerable to hackers. Because of the open nature of these networks, any of your data can be intercepted by others. A VPN is a service that encrypts your online traffic so that others cannot intercept it while you are using a public network, such as a Wi-Fi connection.
Use a Password Manager
Passwords that are both challenging and unique are, more thoroughly, the main line of defense. It’s easy to fall into the trap of using the same weak password for multiple accounts because it’s easier than remembering hundreds of different ones. This is easy for hackers because a single password can unlock several accounts. Instead, you should utilize a password manager that can generate and securely keep your passwords. We recommend Bitwarden as it’s free and easy to use.
Don’t Click on Ads on Torrent or Similar Sites
Clicking on these advertisements could lead you to malicious websites or result in malware being downloaded onto your device.
Keep your phone updated
If you regularly upgrade your operating system, you’ll get any necessary security patches. Your device is more at risk of being attacked if you don’t keep it up-to-date.
Closing Thoughts
A hacked phone can significantly threaten your personal and financial information. Therefore, immediately removing the hacker from your phone and securing your data is crucial. Changing passwords, deleting suspicious apps, using antivirus software, contacting businesses, managing Wi-Fi, and performing a factory reset are some of the effective measures you can take. Additionally, being mindful of your digital behavior, keeping your phone and apps up to date, and avoiding public Wi-Fi can help prevent someone from hacking your phone again. Following these tips can protect your phone and personal information from potential hackers.